|
|
Although the analytical computer was theorised by Alan Turing in 1936, some of his work was critical in the devices used for decryption of messages created by the Enigma machines of the Axis Powers: his "bombes" and the later Colossus were the first computers. Encryption, therefore was part and parcel of the birth of the computer. Colussus was destroyed on orders of Churchill, but was rebuilt at Bletchley Park by Tony Sale.
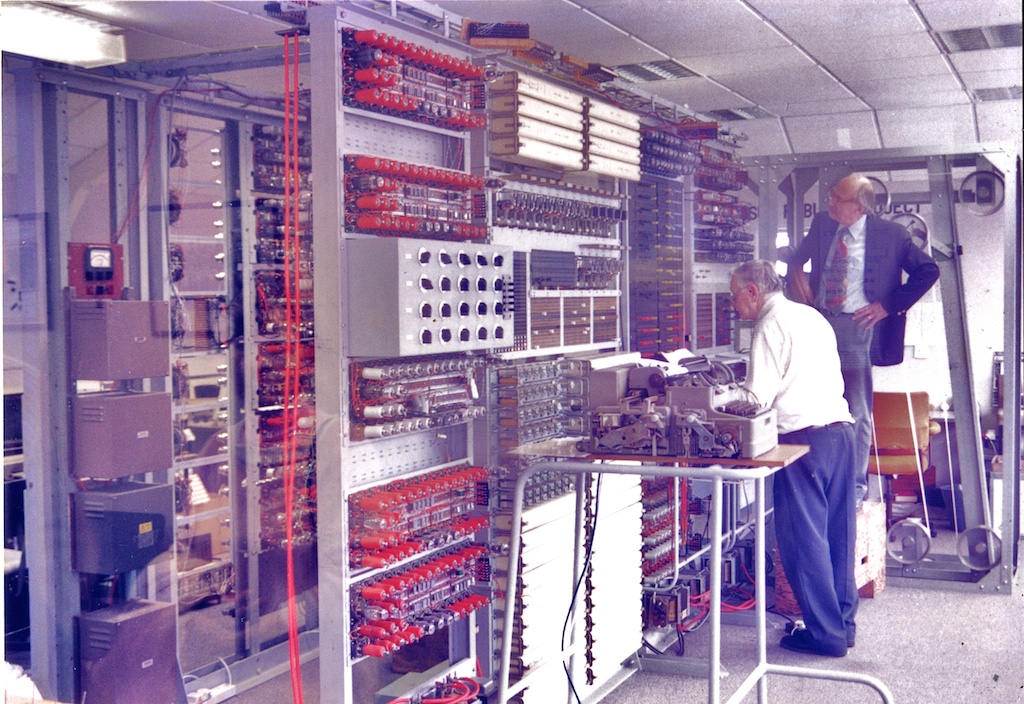
Rebuilding Colossus: Tony Sale at Work - ©Graham K. Rogers
The subject has recently come to the fore with the arrest in New York of several persons who had been spying for Russia. Several of the allegations involved "dead drops", personal wifi networks (so easy to do these days), and the use of steganography. I am teaching a course in which some knowledge of such techniques appears. I have downloaded six applications that can run on OS X, plus one for the iPhone. These hide data inside the file and should not be confused with watermarking although there may be some similarities.
The encryption section on the iPhone offers two sources: camera or library. After selecting a picture and entering a password, I typed a message. After entering a small amount of text -- like an SMS message -- any change, such as a spelling correction, caused the text box to float down (or up) and it became difficult to enter more. Copy and paste (I used a book) is easier. The encrypt button is pressed and the process takes a few seconds only. The image created is stored in the app's own library and can be downloaded by turning on the Server button in the Configuration panel and using a browser connection: the IP number of the phone via port 5555. The image exported had the same dimensions as the original (1600 x 1200 pixels), but fewer colours: file size was smaller. Decryption was easy enough once the password was entered, and the message retrieved was correct.
The OS X version will also decode images from the iPhone app. It opens with a simple panel for loading an image and typing in a password It is also much easier to enter text on this version. I included the first three paragraphs of this article in a 934KB image. The encrypted image was also smaller (221KB). It could not decrypt the test image from iSteg (below). It also managed to put the same 3 paragraphs into an image of 61KB. When I sent that image by email, StegoSec decoded it on the iPhone.
Size is important here, both of the image and the text. Too much text cannot be used inside an image. An image of 934KB would not work with this complete article, but was fine with the 3-paragraph introduction. The clues to the processing are in the feedback panel that shows problems and results. This was like the processes shown by Hugin, the Open Source-based panorama software. To decode an image, the user unchecks the Encode box and selects the image file. With the right password entered the process creates a text file. In the brief tests I carried out, retrievals were error free.
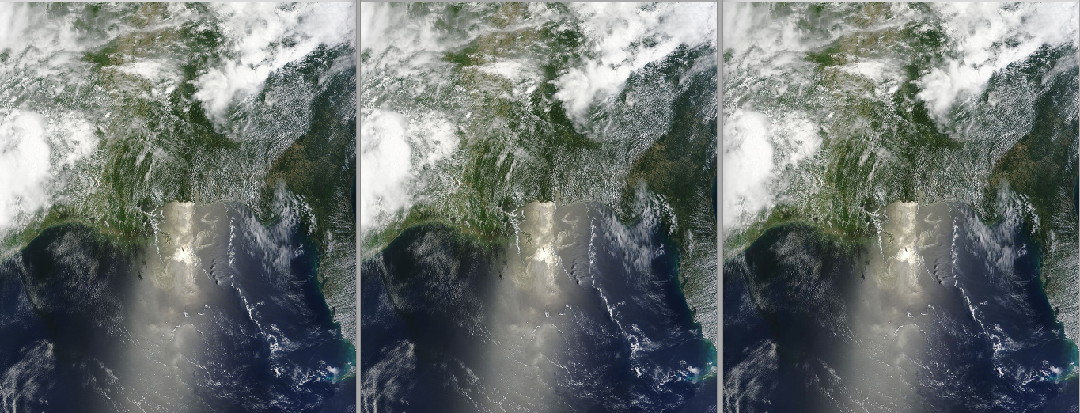
Original image; encrypted by iSteg; and encrypted by StegoSecOsX
|
|

 The iPhone app, StegoSec, is a $1.99 download (65 baht). After its eerie opening screen, we are shown a panel for decryption. It is no use encrypting images unless someone else can read the message. There is also a version of this for OS X:
The iPhone app, StegoSec, is a $1.99 download (65 baht). After its eerie opening screen, we are shown a panel for decryption. It is no use encrypting images unless someone else can read the message. There is also a version of this for OS X: 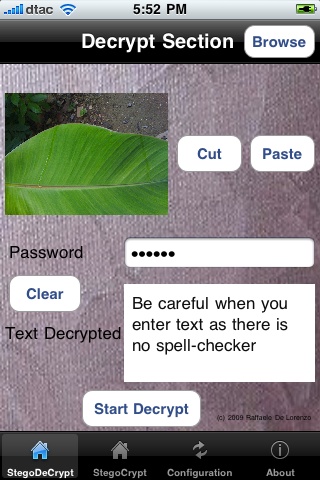 I initially thought that there was no email function but, confusingly, in the Decrypt section, by pressing the Cut button (next to Paste) a panel appears allowing email, SMS or "Cut in Clipboard". To make this useful there needs to be someone at the other end, with the same software, and the right password.
I initially thought that there was no email function but, confusingly, in the Decrypt section, by pressing the Cut button (next to Paste) a panel appears allowing email, SMS or "Cut in Clipboard". To make this useful there needs to be someone at the other end, with the same software, and the right password.

