 The portable document format, or pdf is a cross-platform document. Before Tiger, when downloaded via a link, these opened either in Preview or in Adobe Acrobat. Now, the file is downloaded and opens in a Safari page.
The portable document format, or pdf is a cross-platform document. Before Tiger, when downloaded via a link, these opened either in Preview or in Adobe Acrobat. Now, the file is downloaded and opens in a Safari page.|
OSX (10.4) Tiger: A few days more |
Apple advertised over 200 improvements to Tiger. Most are invisible. We have seen the eye-candy of Dashboard Widgets: a technology in-waiting. Apple's own presentations have heavily pushed Spotlight, which does make searching easier: start typing a word and thousands of results appear. These are reduced as the word is typed fully. Then every reference -- text, file names, mail messages -- is offered. Most changes to Tiger have occurred under the skin and I have been digging some of these up.
 The portable document format, or pdf is a cross-platform document. Before Tiger, when downloaded via a link, these opened either in Preview or in Adobe Acrobat. Now, the file is downloaded and opens in a Safari page.
The portable document format, or pdf is a cross-platform document. Before Tiger, when downloaded via a link, these opened either in Preview or in Adobe Acrobat. Now, the file is downloaded and opens in a Safari page.
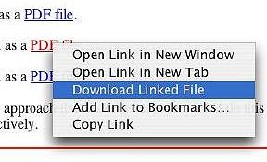
For many users, that is enough, but often a pdf is large and it is better viewed at one's leisure. Apple has provided alternatives. To download the pdf directly to the desktop, click on the link while pressing the Control key. This displays a panel with options, including downloading. If the pdf document is open in Safari, to view it in Preview, use Control Click and choose that option; and if you want to save it, choose the File menu and "Save As".
My office, and some places I visit (Siam Discovery Center, Central World) have Wi-Fi. Usually, I wake the PowerBook and the connection is identified. I have previously accepted these links, so connections are automatic.
I had a hiccup in the office: I linked to a repeater, put the computer to sleep, and after lunch started work again. I should have been connected to the main WiFi outlet, but this has the same identifying name as the repeater. After a couple of attempts I was ready to restart the Airport on the PowerBook, when a page in Safari appeared and told me that something was awry: would I like to try "diagnosis"?
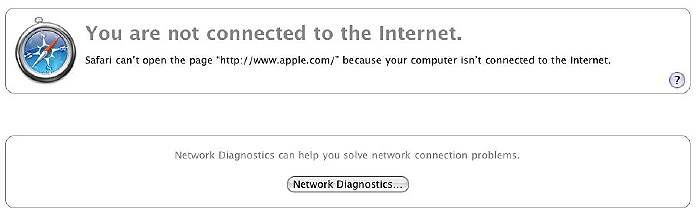
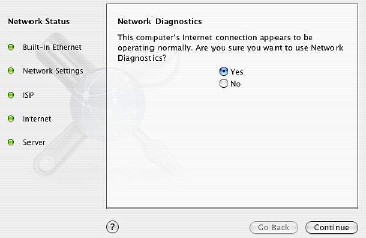
The software searched for links, then asked a series of questions to confirm my settings. Diagnosis: you are connected to the wrong one. Cure: would you like to link to the right one? The link was automatically re-established and happiness was restored.
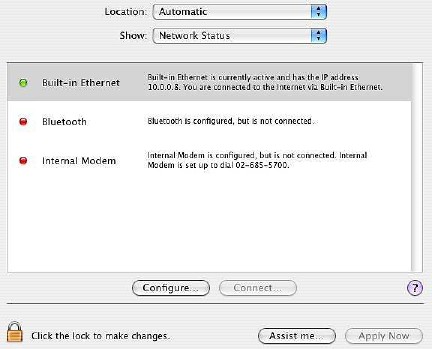
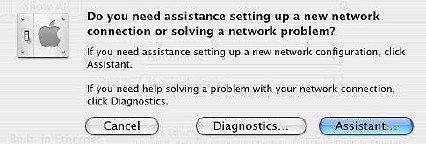
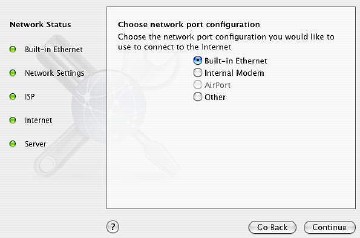
The ability to diagnose networking problems, however the connection is made, can also be accessed through the "Assist Me" button in Network Preferences. The Assistant helps with a new configuration, while Diagnostics solves problems with a current set up.
|
|
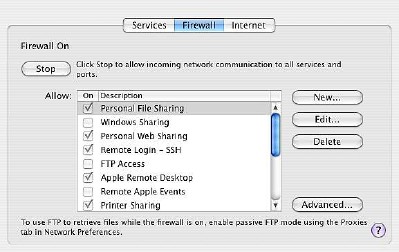
We hear much about security nowadays: valid warnings. As I link my laptop to a number of networks, as soon as the computer was in my hands, I turned on the firewall. While some ports are open by default, I am also able to select ports that I need open for access to specific services.
Tiger has some new Firewall features and users may consider turning these on. In the Firewall panel of Sharing Preferences, there is a new "Advanced" button. Selecting this brings up an additional panel with three selections: Block UDP traffic; Enable Firewall logging; Enable stealth mode.

|
|
UDP (User datagram protocol)
The Firewall log, can be accessed through a button on that samel panel. In two or three days, I saw that Apple Computer had several goes; Lycos tried; and there were frequent pings from Asia Pacific Network Information Centre -- the link from True. It also shows the number of times I connected (or tried, see below).
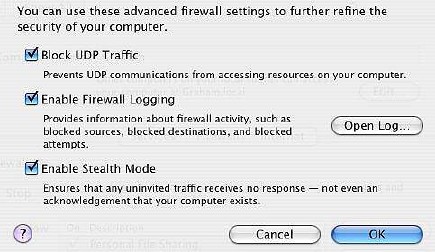
The basic purpose of Enabling Stealth Mode is to make your computer invisible to other computers, so this adds major security to your computer when linked to any network: if it cannot be seen, no one will try to break in (similarly with Apple's Root, no software in the world can guess a non-existent Root password).
If you have a system like mine where I work with two computers and sometimes transfer data between them, trying to log-in cannot be done as before with the Go menu in Finder (afp://10.xx.xx.x) as, even to the "friendly" PowerBook downstairs, my eMac is invisble. However, it is now possible within the network to use ssh (secure shell) to link the two using "ssh username@10.x.x.x".
With each of these new Firewall settings, there are pluses and minuses. Use of each has to be a decision that the user makes.

For further information, e-mail to Graham K. Rogers.
Back to
eXtensions
To
eXtensions: Book Reviews
To
eXtensions: Year One
To
eXtensions: Year Two
Back to homepage