|
|
eXtensions
|
The Virus and OSX |
Note (added 21 Feb 2006): I have seen the number of hits to this page increasing in the last few days. Tthere have been reports this week of a virus/worm/trojan for OS X that spreads via iChat -- Leap-A. Although many commentators suggest it is not over-serious (including Apple), there is also a feeling that the long weekend is over. That may be. Reports suggest that the files needed user help in some cases -- either to be downloaded and/or installed. Damage done by the attack was minimal. The security companies updated their definitions (including Mark Allan -- see below -- who produces ClamXav). The other insecurity was one that based itself on a weakness in Bluetooth that was fixed a while back. Do not be complacent; and please do secure your computer with proper passwords.
There are no OSX virusus (or worms, or Trojans): partly due to the implementation of OSX and its almost-inaccessible Root. Dr Smoke, who gave me some advice on this subject, gives a clear explanation of how the problem should be viewed at the X Lab pages.
Most Mac users never need Root access. We use Administrator privileges and, if Root is needed for installation of an application or for alterations to the system -- what a virus would need to do -- a user must enter a password: physically and consciously acknowledging an event (and its consequences).
Mac naysayers would have us believe there are no viruses because there are so few Macs (this also applies to Linux and Unix platforms), although that could change with the iMac mini. If the numbers of viruses for Windows keeps on growing (15 Jan 05; Total Viruses Detected 68736 -- Symantec) the Mac may come in for some attention. There is no point spending all your time virus-writing, however, if viruses will not work.
The only problem on OSX is from macros with Microsoft products and from mail attachments. These do not harm the Mac environment but may damage a Windows computer if sent. As a normal precaution I do not open attachments, and trash them instantly.
This immunity may not last. There have been experiments: last year one (one!) widely-reported Unix-based package was found: it had no method of self-propagation and no delivery system.
I almost long for the days (and simplicity) of the locally-written Victor Charlie (for DoS) which examined checksums to seek out unauthorised changes. (Note: try a Google search using keywords: Victor Charlie+DOS+Bangkok.)
A virus signature -- the common method of virus-detection these days -- may arrive days after the event. There is a Unix-based system integrity checker, called Tripwire, which I installed (see xnote7). I would not suggest installing this unless you are really comfortable working at the command line. This is one that screams out for a GUI version.
What we have left, if we are going to prepare, are the signature checkers. McAfee Virex has been around for a long time -- I used a copy in System 8 -- and can be found as part of the .Mac subscription. It was withdrawn by Apple in late 2004 for a brief time after a conflict was discovered and is now available again with .Mac. It is also on sale. Some users still report problems.
Norton Anti-virus for Mac, version 9.0 is also in the market and has a good following. A number of OSX users have also installed the products of Intego: these include VirusBarrier and Netbarrier. A further commercial product is that of Sophos which has a link to evaluate a copy of the application. This is aimed at larger enterprises.
Mark Allan, from the UK, had been using an Open Source application called ClamAV but he tired of the command line so, bless him, took it upon himself to develop ClamXav, a free virus checker (using signatures). Version 0.9.0f for OSX is a 2.8MB download with a simple install process.

|

|
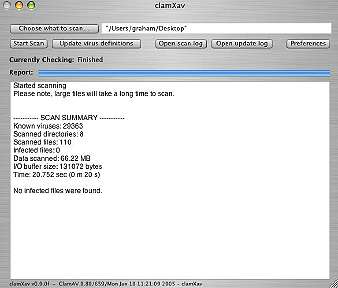
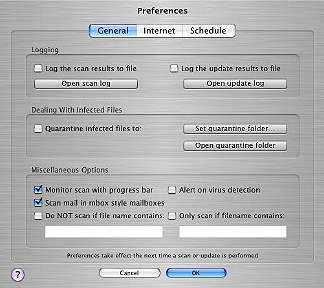
A panel allows you to update the signatures (you can also set this to update automatically) and a file browser gives you choices of which directories or files to scan. Preferences are available for some fine-tuning: General, Internet and Schedule. The software has the ability to move infected files to a quarantine folder where they can be isolated. Items that can be scanned include mailboxes: Mark includes a warning that, for these, the isolation method should not be used. The mailbox needs to retain its integrity.
I ran ClamXav three or four times, first on a small selection of files, then some larger directories and also mailboxes. Half a dozen Word files that I had not used in about three years were shown as having Macro viruses. As I do not use Word, these had not come to light earlier (nor had they spread). ClamXav does not repair infected files: I opened them in TextEdit, copied the text information and dumped the originals. Problem solved.
|
|
Mark's website has some useful information on this utility and makes it clear that, although free, a donation migh be appropriate. There is a "nag" screen for this that comes up occasionally. For what it does, ClamXav is rightly getting some good reports from the online Mac community. It is never too early to lay the foundations for a warning system.
Note: as well as the macros, a later check identified an example of phishing that I had deliberately saved in my mailbox, perhaps demonstrating more that ClamXav has its uses even if viruses are not a problem for OSX users. Let me also repeat, if you are checking the mailboxes, it is strongly suggested that the quarantine facility not be used.
Note (for Windows persons): I got this from the Open SourceForge newsletter. ". . . the ClamAV scanning engine used in the ClamWin Free Antivirus has been updated to version 0.81. As the result ClamWin version 0.37.4 now shows an "outdated" warning when updating virus database. New ClamWin Free Antivirus version 0.37.5, which upgrades ClamAV antivirus engine has now been released. Please download it using this link http://prdownloads.sourceforge.net/clamwin/clamwin-0.37.5-setup.exe?download"

For further information, e-mail to Graham K. Rogers.
Back to
eXtensions
To
eXtensions: Book Reviews
To
eXtensions: Year One
To
eXtensions: Year Two
Back to homepage