Cassandra: Never Going to Give up - Phishing, Malware and the Zip File

AMITIAE -Friday 18 October 2013
|
Cassandra: Never Going to Give up - Phishing, Malware and the Zip File |
 |
|
|
By Graham K. Rogers
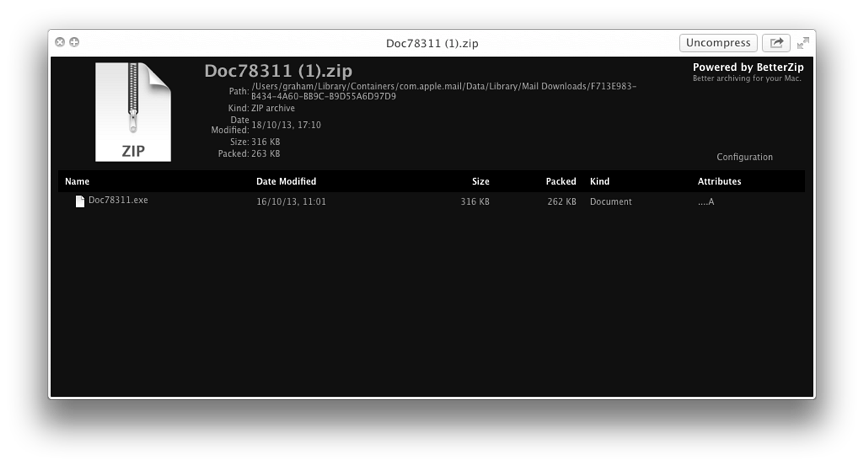
My rule here is that, if I do not know you and you are sending me files, the email and the package go in the trash. Occasionally, the emails purport to come from someone I know. This has happened twice recently. A colleague with whom I have little content was allegedly in Egypt, all belongings stolen and in need of my largesse. As she has far closer friends in a better position to help, I smelled a rat. Another colleague confirmed this. A similar email this week (a few months after the first) was duly dumped. Also this week saw the arrival of a rather gaudy circulation offering me (and others to whom it was addressed) amazingly cheap travel deals. This was due to the lifted contents of an in-house mailing list. A friend offered to assist the department involved tighten its security. Sometimes there is a spark of innovation with these emails, although half a dozen at the same time with similar wording, are usually enough to arouse my suspicions. Some users are sadly not as mistrusting as me. I am occasionally sent emails starting with, "I know I shouldn't have done, but I clicked on an attachment and. . . ."

More to the point, save your computer, think before you click.
Fortunately, there is a nice little utility from MacItBetter called The BetterZip Quick Look Generator, which is now up to version 1.2. As well as ZIP files, this can look inside TAR, GZip, BZip2, ARJ, LZH, ISO, CHM, CAB, CPIO, RAR, 7-Zip, DEB, RPM, StuffIt's SIT, DiskDoubler, BinHex, and MacBinary. This is really useful because if you click on some files, the damage is already done.
Library? That seems to be missing. Apple hides this nowadays in User accounts, so the Finder "Go" menu needs to be used. In the Home folder, use "Go to Folder" and type in the name Library. If there is no QuickLook folder, make one: Shift+Command+N does this, and then enter the name (with upper case Q and L). If all users are to have access to this (or you only work in the Admin account - I question your security credentials), the QuickLook folder is found in the ~/Library/QuickLook folder. The website gives some information about making it start work on first installation including using either the Terminal command "qlmanage -r" or by logging out and back in again.
I wonder what little trick that had inside it. I also wonder how many computers it did work on. . . .
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand where he is also Assistant Dean. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. |
|

For further information, e-mail to

|

|