Enigma, Stuxnet and Piracy: Questions on Ethics and Morals for Computer Engineers

AMITIAE - Sunday 6 January 2013
|
Enigma, Stuxnet and Piracy: Questions on Ethics and Morals for Computer Engineers |
 |
|
|
By Graham K. Rogers
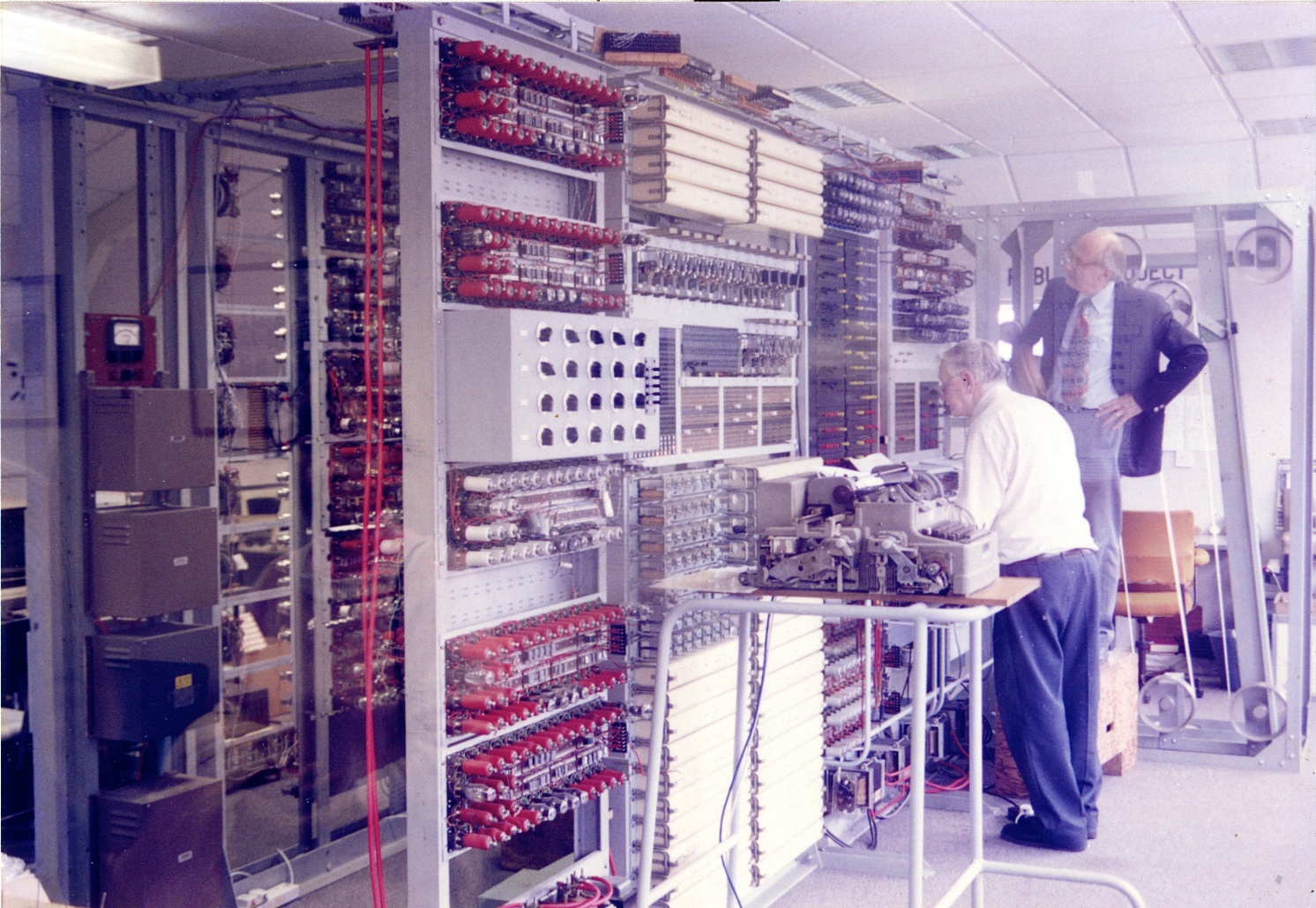
The purpose of Colossus, and the earlier Bombes developed by Alan Turing was to break code. Tactical communications between units of the German forces and the High Command were coded by a rather clever device called Enigma and the coded messages were impossible to crack by conventional means. No one has ever suggested that Colossus or the Bombes were not ethical or moral developments (and I am certainly not going to do that now). I have no doubt that the Enigma encryption system was also completely ethical. A nation at war has a duty to counter the enemy by the means at its disposal. Chemical or biological warfare may be at hand for many governments, but its use is generally considered immoral. For now.
It was certainly unethical as the intent was to cause certain effects to a system, but there is a borderline call on the morality of the action: irresponsible for sure. There is evidence to suggest that Morris never intended the Worm to spread in the way it did, and had no idea of the way so many systems would be overloaded and shut down: a lesson still not properly learned.
In the Executive Summary of their Security Response on W32.Stuxnet, Symantec make it clear that this is no ordinary piece of malware and its intent is "to reprogram industrial control systems" such as those "used in gas pipelines and power plants". Iran was targeted it is believed because of its nuclear program, but the worm has now spread to several other countries, notably Indonesia and India. With Malaysia also shown in the statistics, there may be some risk to Thailand: the Electricity Generating network main control system does not appear to use Windows; but Bangkok's BTS (SkyTrain) uses much equipment from Krupp and Siemens. The malware is introduced (perhaps unwittingly) via a flash drive or other removable device and then spreads via LAN. The report does not name any country or organisation responsible for Stuxnet, but notes in the Summary that "Stuxnet is of such great complexity - requiring significant resources to develop - that few attackers will be capable of producing a similar threat. . . ."
However, in an article confirming this by Nate Anderson on Ars Technica, the sub-heading has an unlearned lesson: "Stuxnet was never meant to propagate in the wild," a lesson that was there for all to see from the Morris Worm. Things do not always go according to plan.
Other questions to be raised in the short course concern Steganography (hiding data inside image files), Data Mining, Hacking, Privacy & Civil Liberties and Economic Issues (patents, trademarks, piracy).
When I first arrived here in the late 1980s, it was easy to buy a PC. Buying legal software was another matter as the developers - especially the largest companies - would not sell their products here. Trying to buy from another country (pre-Internet) was not easy, and the moment the address was given, the deal was off: cannot ship to Thailand. With computers, but no software, what do people do? . . .
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. |
|

For further information, e-mail to

|

|